The acronym VPN stands for “Virtual Private Network”. Used often by employees working from home, a VPN connection allows employees to remotely and securely connect to your business’ network. It creates a secure tunnel between their computer and your corporate network. The individual (or employee) will have access (depending on your network policies) to all the same resources, as if they were plugged directly into your network!
How does a VPN connection for business work?
Connecting using VPN for business needs 3 parts:
- the employee working from outside the office, with the proper software installed on their device;
- a secure VPN connection using the Internet; and
- some sort of resources at the office, such as a server.
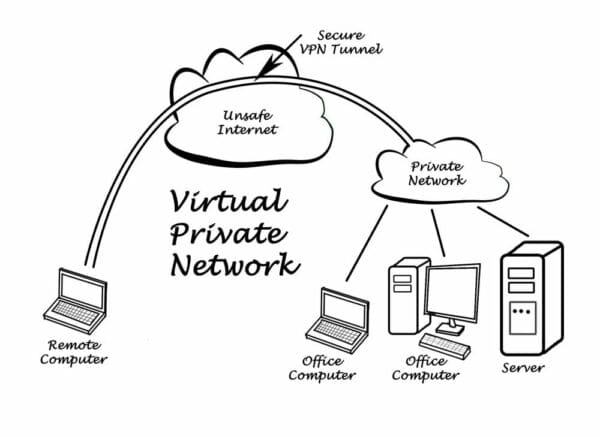
Your server at the office connects to a private network, as do any other devices connected to the network. This is where the data for your business is stored, and what the individual will connect to by using the Internet and the VPN. When an employee wants to access the data that is at the office, from a location outside of the office, a VPN gives them a secure tunnel through which to access the data.
Why use a VPN?
There are multiple reasons why a company would implement a VPN for their employees.
The first reason is to protect remote employees when they are on the road (airport, coffee shop, hotel) and using open Wi-Fi networks from Starbucks or Tim Hortons (We’re proud Canadians!). This ensures that all of their web traffic is encrypted and nobody can “snoop” in on what they’re doing, and steal passwords when sent over unencrypted communications. If you don’t have the time, money or interest to implement a VPN for this reason, then there’s a long list of outsourced VPN providers who provide this type of service at a low monthly cost. Be careful to choose a trustworthy company as they are now brokering all of your web traffic through their servers.
The second reason to use a VPN is to allow remote employees to access corporate resources such as file servers or applications that reside on the company’s internal network and require special authentication to use them. For example, a large percentage of our clients are in the healthcare industry and use an Electronic Medical Record (EMR) system that resides on a local server inside their offices. As such, they require a secure VPN connection to gain access to their business system.
With the COVID-19 pandemic, an increasing number of companies are now using secure VPN connections for their business, as the amount of employees working remotely is growing. Some key benefits of employees working remotely include improved employee retention and increased productivity due to less time commuting, and an environment that has fewer distractions.
Do all companies require VPNs?
No, not at all. It depends…
From what we’re seeing in our client base, more and more companies are moving their on-premises servers to Cloud-based solutions (MacOS servers to OneDrive, CRMs, etc.) and as such don’t have a need for VPN.
If you’re looking to protect your remote users web traffic, there are certainly other light solutions that can offer similar protection and don’t require the extensive set up of a VPN.
Which VPN solution do you recommend?
That’s a great question and as they say “it depends”. However, SonicWALL is our preferred product line as we’ve deployed it hundreds of times and it provides a robust, secure and reliable VPN experience for our customers. In addition to its Next-Generation Firewall security services, it provides built-in VPN services.
SonicWALL has a variety of options to choose from. The SonicWALL TZ series of products are great for small offices requiring basic L2TP or SSLVPN. The SonicWALL NSA series is meant for larger environments (40+ users), and finally the newly released SonicWALL Secure Mobile Access (SMA) is a dedicated appliance for SSLVPN. One thing to consider when implementing VPN is Multi-Factor Authentication and ensuring your solution integrates with your Directory Services (AzureAD, ActiveDirectory or LDAP).
Best Practices / Quick Tips
- FIREWALL SIZING – Ensure your Firewall or VPN appliance is properly sized to ensure there are now slowdowns or disconnections for your users.
- LICENSING – Depending on your vendor, ensure you have enough VPN licenses assigned so that you don’t run into “out of licenses issues”.
- USER DIRECTORIES– Don’t double the work, make sure your VPN solution can integrate with your existing directory of users (AzureAD, Okta, OneLogin, LDAP, ActiveDirectory, OpenDirectory anyone?) The moment an employee leaves, disabling his account within your main user directory would also disable his VPN access.
- MULTI-PLATFORM – Pick a vendor that offers multi-platform support including macOS, Windows, Android and iOS. Is the VPN client app available from Apple’s App Store or the Microsoft Store? How often is that app updated? Do they offer zero-day support when new operating systems are released? These are important considerations that will impact the deployment of the solution.
- MULTI-FACTOR AUTH (either in the form of One-Time Password (the cool kids call it OTP), or an authenticator app is highly recommended!
- SECURITY – Segmenting access to internal resources based on group membership is also very important and should be considered during the solution design. Do you want your physicians to have access to your entire internal network (servers, printers, switches) or just the server that runs their medical software?
- DEPLOYMENT – How will the VPN client be deployed to your users devices? If you’ve got dozens or hundreds of users that may not be an easy task to put in the hands of your users. Of course, having a Mobile Device Management solution in place makes that whole process much easier.
- BEST ADVICE – From experience, SSLVPN solutions appear to be more reliable and easier to manage than the antiquated L2TP over IPSec (or better yet PPTP!). They are also less likely to get blocked in public Wi-Fi networks.
- GUIDE – We put together a quick guide on how to configure a L2TP on macOS.
Need help with this VPN mumbo jumbo?!
As you can see, there are lots of things to consider when deploying a VPN solution for your company. As always, our team remains available for consultations and assistance in deploying a drama-free solution. Contact us today!
